
How to Achieve NIS2 Compliance: What Businesses Need to Know

In 2016, the European Union Agency for Cybersecurity (ENISA) established the original Network and Information Security directive (NIS directive) to lay the groundwork for EU-wide cybersecurity measures. Since networks and systems are largely interconnected in the EU, the directive aims to fix weaknesses that could result in widespread disruptions or data breaches.
In January 2023, Directive (EU) 2022/2555, also known as the NIS2 Directive built upon its predecessor to improve cybersecurity across EU member states among growing cyber threats. NIS2 expands its scope, introducing stricter security requirements and broadening the range of sectors required to comply.
In short, NIS2 is designed to enhance the cybersecurity and resilience of organizations providing critical infrastructure and essential services. It applies to organizations in sectors like energy, transport, banking, health, water supply, digital infrastructure, and public administration.
All relevant organizations are expected to comply with the directive by October 17, 2024. Is your business one of them?
Table of Contents:
Which Businesses Need to Comply with the NIS2 Directive?
The Directive applies to organizations based on these criteria:
- The sector they operate in
- The size of the company
Which sectors need to comply with the NIS2 Directive?
The NIS2 Directive categorizes entities into essential entities and important entities. Organizations in both categories will have to meet the same requirements. However, the difference lies between how compliance of these 2 groups will be supervised and penalized.
While essential organizations will be proactively supervised to ensure they meet the requirements of the NIS2 Directive, important organizations will only be investigated after authorities receive evidence of non-compliance.
You can find a simple overview of essential and important entities by sector they operate in in the chart below. You can find the full breakdown of each sector and their subsectors in Annex 1, page 64 of the NIS2 directive.
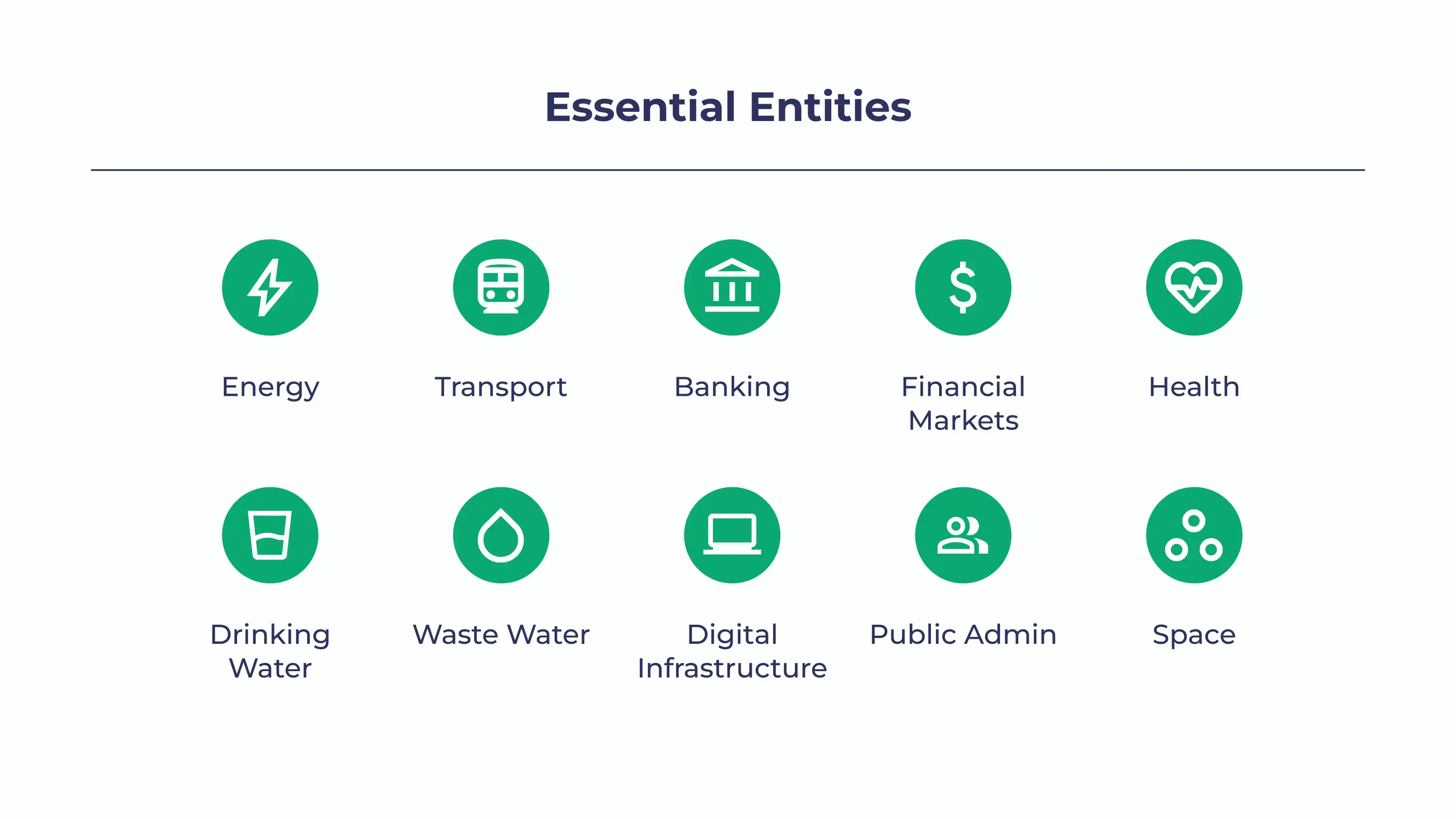
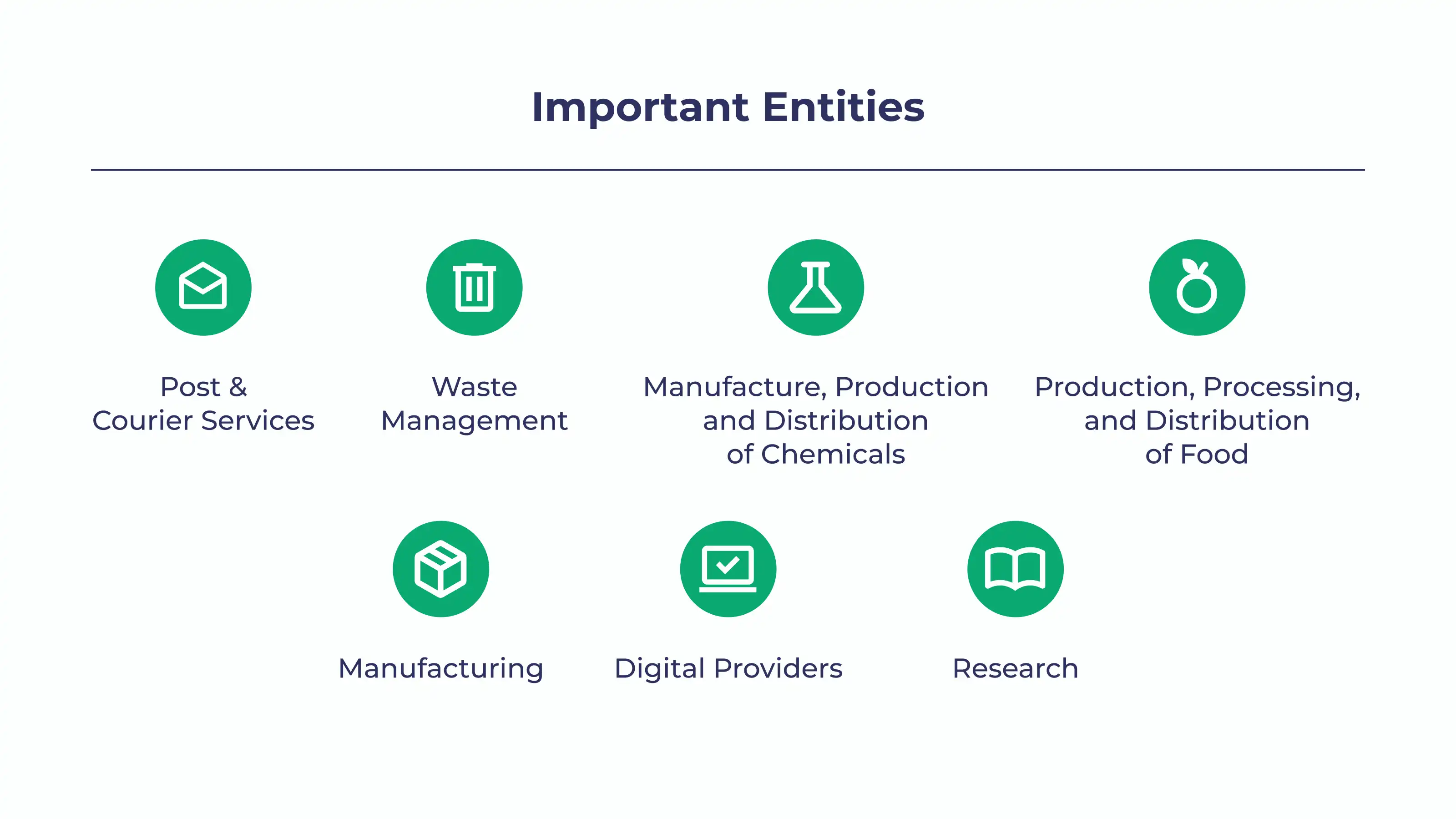
What are the size criteria for compliance with the NIS2 Directive?
In general, your organization is required to comply with the NIS2 directive if it belongs to one of the sectors outlined above, and fits into these size categories:
- Large enterprises: companies with a headcount over 250, revenue of more than 50€ million, or balance sheet greater than 43€ million
- Medium enterprises: companies with a headcount over 50, revenue of more than 10€ million, or balance sheet greater than 10€ million
However, it is important to keep in mind that these rules vary by sector.
Does that mean that small and micro enterprises are excluded? Not necessarily - smaller organizations within the designated sectors may still be subject to compliance if the countries they operate in consider them to have a significant impact on critical infrastructure or essential services.
Lastly, if your organization is located outside of the EU, you may still be subject to the NIS2 directive if you operate within the EU and meet the criteria outlined above.
It is always best to consult with legal experts or regulatory authorities to determine your specific obligations under NIS2, as compliance requirements can vary depending on factors such as sector, size, and geographical location. Learn how heyData can help you determine if you need to comply with the NIS2 directive here.
Now, let's take a closer look at the focus points of the NIS2 Directive.
5 Key Focus Areas of the NIS2
By concentrating on these requirements and focus areas, the directive intends to increase Europe's resilience against current and future cyber threats:
1. Risk Management
Risk management is a key part of the NIS2 Directive. It focuses on taking proactive steps to find, evaluate, and reduce cybersecurity threats. Good risk management practices are crucial for protecting an organization's assets and keeping operations running smoothly.
These measures include:
- Incident Management: Establishing an incident response plan to quickly and effectively address cyber incidents, minimizing their impact and preventing further damage. For example, a company might discover that its customer database has been breached. With an incident management plan in place, the company can immediately isolate the affected systems, notify its customers, and work with cybersecurity experts to contain and resolve the breach, minimizing financial losses and reputational damage.
- Stronger Supply Chain Security: As cyber threats often take advantage of weaknesses in interconnected networks, organizations will be responsible for addressing cybersecurity risks in their supply chains. As such, suppliers who are not directly in the scope of NIS2 may be indirectly impacted and supervised by their customers. Organizations are therefore advised to conduct thorough evaluations of third-party services to identify potential cybersecurity weaknesses leveraging services such as Vendor Risk Management from heyData.
- Network Security: Organizations will be required to implement robust network security measures, including secure configurations, continuous monitoring, and regular vulnerability assessments. This will help prevent unauthorized access to sensitive data and ensure the integrity of critical systems.
- Better Access Control: Implementing strong access control mechanisms is essential for minimizing the risk of unauthorized access to sensitive data and systems. This includes multi-factor authentication, role-based access controls, and regular user access reviews.
- Encryption: Encrypting sensitive data at rest and in transit is crucial for protecting it from unauthorized access. By using strong encryption algorithms, organizations can ensure that even if data is intercepted, it remains unreadable and unusable to attackers. For example, a healthcare provider might encrypt patient records stored on their servers and the data when sent to other healthcare facilities. This way, even if a hacker intercepts the transmission or gains unauthorized access to the server, the encrypted data would be useless without the decryption key.
By implementing these measures, organizations can strengthen their cybersecurity posture and better protect themselves against evolving cyber threats.
2. Corporate Accountability
Corporate accountability is central to the effectiveness of the NIS2 Directive as top management plays a crucial role in ensuring compliance with NIS2 standards.
A notable example of corporate accountability in action is the case of Equifax. In 2017, Equifax CEO Richard Smith had to publicly take accountability after a massive data breach that exposed the personal information of approximately 147 million people. This led to Smith stepping down from his position and appearing before Congress to address the failure, significantly impacting the company's reputation and stakeholder confidence.
According to NIS2 directive, the management of an organization must:
- Establish and enforce cybersecurity policies: Leadership should oversee, approve, and be trained on robust cybersecurity frameworks that align with NIS2 requirements.
- Conduct regular risk assessments: Continuous evaluation of potential threats is essential. This involves identifying vulnerabilities, assessing their impact, and implementing mitigation measures.
- Ensure staff training: As employees are often the weakest link in an organization's cybersecurity defense, consistent training sessions not only enhance compliance but also improve an organization's overall security posture.
The commitment to these practices fosters a culture of accountability within organizations. This culture ensures that all employees, from top management to entry-level staff, prioritize cybersecurity.
Effective corporate accountability instils a proactive approach to managing cyber risks, thereby reducing the likelihood of significant incidents. Additionally, breaches can result in severe penalties for management including liability, and even temporary ban from management positions.
3. Reporting Obligations
Incident reporting is a critical aspect of the NIS2 Directive, designed to ensure timely communication and response to cybersecurity threats. Organizations must adhere to strict compliance deadlines for reporting significant cyber incidents to the relevant national authority. This promotes transparency and allows for a coordinated response to emerging threats at a national level.
The NIS2 Directive outlines these instructions for how security incidents should be reported:
- Within 24 hours of becoming aware of an incident: the organization should notify the relevant national authority, providing a high-level summary of the incident, its impact, potential cross-border consequences, and the actions taken or planned to address it.
- Within 72 hours of becoming aware of an incident: a detailed report must be submitted, including comprehensive information about the incident, its root causes, affected systems or data, and any mitigation measures implemented.
The much stricter 24 and 72-hour hard deadlines under NIS2 require organizations to have near real-time threat visibility and efficient reporting procedures in place. Failure to comply with these reporting obligations can result in significant penalties, including fines and reputational damage.
By enforcing strict reporting requirements, the NIS2 Directive aims to enhance incident response capabilities, facilitate information sharing among member states, and ultimately strengthen the overall cybersecurity resilience of critical infrastructure across Europe.
We can find an example that demonstrates the importance of timely incident reporting in the 2017 WannaCry ransomware attack and its impact on the UK's National Health Service (NHS). The WannaCry ransomware rapidly spread across computer networks worldwide, exploiting a vulnerability in older Windows operating systems. The attack significantly affected the NHS, disrupting hospital operations and patient care across England and Scotland. While the initial impact was severe, the quick reporting and response helped mitigate further damage - within hours, NHS Digital, the national information and technology partner for the health and care system, detected the attack quickly and alerted NHS organizations. The National Cyber Security Centre (NCSC) was immediately engaged, working closely with NHS Digital and other government agencies to provide expert advice and support. This quick detection and reporting helped limit the attack's impact as ultimately only about 1% of NHS organizations were infected, the majority of NHS services remained operational throughout the incident and no patient data was compromised.
4. Business Continuity
Effective business continuity planning ensures that organizations can continue important functions during and after a cybersecurity incident. It's not just about recovering but also about keeping operations running under pressure.
A business continuity plan should include:
- System recovery: Restoring affected systems and data to their normal state, ensuring minimal disruption to operations. This also includes identifying backup systems or alternative processes to maintain critical functions if primary systems are compromised.
- Emergency procedures: Clearly defined steps outlining immediate actions to be taken in the event of an incident, such as isolating affected systems, activating incident response teams, and notifying relevant stakeholders.
- Crisis response team: An effective incident response team is a crucial component of any cybersecurity strategy. This team should be well-trained, equipped with the necessary tools and resources, and have clear roles and responsibilities.
By combining these strategies, organizations strengthen their business continuity as well as the ability to withstand cyber threats. Organizations are better equipped to deal with disruptions, reducing downtime and financial losses. This proactive approach aligns with NIS2's goals, ensuring that entities are not only reactive but also resilient in the face of cybersecurity challenges.
5. Collaboration Among Member States
Collaboration among member states of the EU plays a vital role in achieving the goals of the NIS2 Directive. The directive encourages cooperation between member states, as well as with relevant stakeholders, such as the private sector and academia. Enhancing cooperation ensures that all EU countries work together to combat cybersecurity threats effectively.
For example, in May 2021 Ireland's Health Service Executive (HSE) suffered a ransomware attack. The incident triggered a rapid collaborative response across EU member states, as Ireland National Cyber Security Center alerted other EU countries, which quickly offered immediate technical assistance and shared threat intelligence to restore critical healthcare systems faster. As a result, the potential impact on patient care was significantly reduced, and the spread of the attack to other EU healthcare systems was prevented. This incident demonstrated how the collaborative frameworks envisioned by NIS2 can enhance cybersecurity resilience across the EU.
The NIS2 Directive enables cooperation by:
- Strengthening ties between member states, allowing for a coordinated and swift response to cyber threats.
- Pooling resources to help mitigate the impact of incidents and enhance overall cybersecurity resilience.
- Establishing common standards and practices across the EU ensures consistency in tackling cybersecurity challenges.
To that end, European Cyber Crises Liaison Organisation Network (EU-CyCLONe) was established aiming to facilitate communications during cross-border incidents, coordinate actions to mitigate crises, and provide critical information to aid national decision-makers.
NIS2 Directive also covers these focus areas in the checklist of 10 minimum measures.
Conclusion
The NIS2 Directive marks a significant step forward in strengthening the cybersecurity framework across the EU. By addressing key areas such as risk management, corporate accountability, reporting obligations, business continuity, and collaboration among member states, the directive aims to create a more resilient digital environment.
As businesses and sectors align with these new requirements, the collective cybersecurity posture of the EU is expected to improve, ultimately safeguarding critical infrastructures and enhancing digital trust across member states.
If your business is among the ones affected by these changes, achieving compliance may seem daunting. heyData offers support for companies aiming to achieve compliance with the NIS2 Directive through its NIS2 Compliance service.


