
Human Weaknesses in Cybersecurity 2025: Risks, Facts, and Solutions
'%3e%3cpath%20d='M26.6667%2020.022L30%2023.3553V26.6886H21.6667V36.6886L20%2038.3553L18.3333%2036.6886V26.6886H10V23.3553L13.3333%2020.022V8.35531H11.6667V5.02197H28.3333V8.35531H26.6667V20.022Z'%20fill='%230AA971'/%3e%3c/g%3e%3c/svg%3e) Summary
Summary
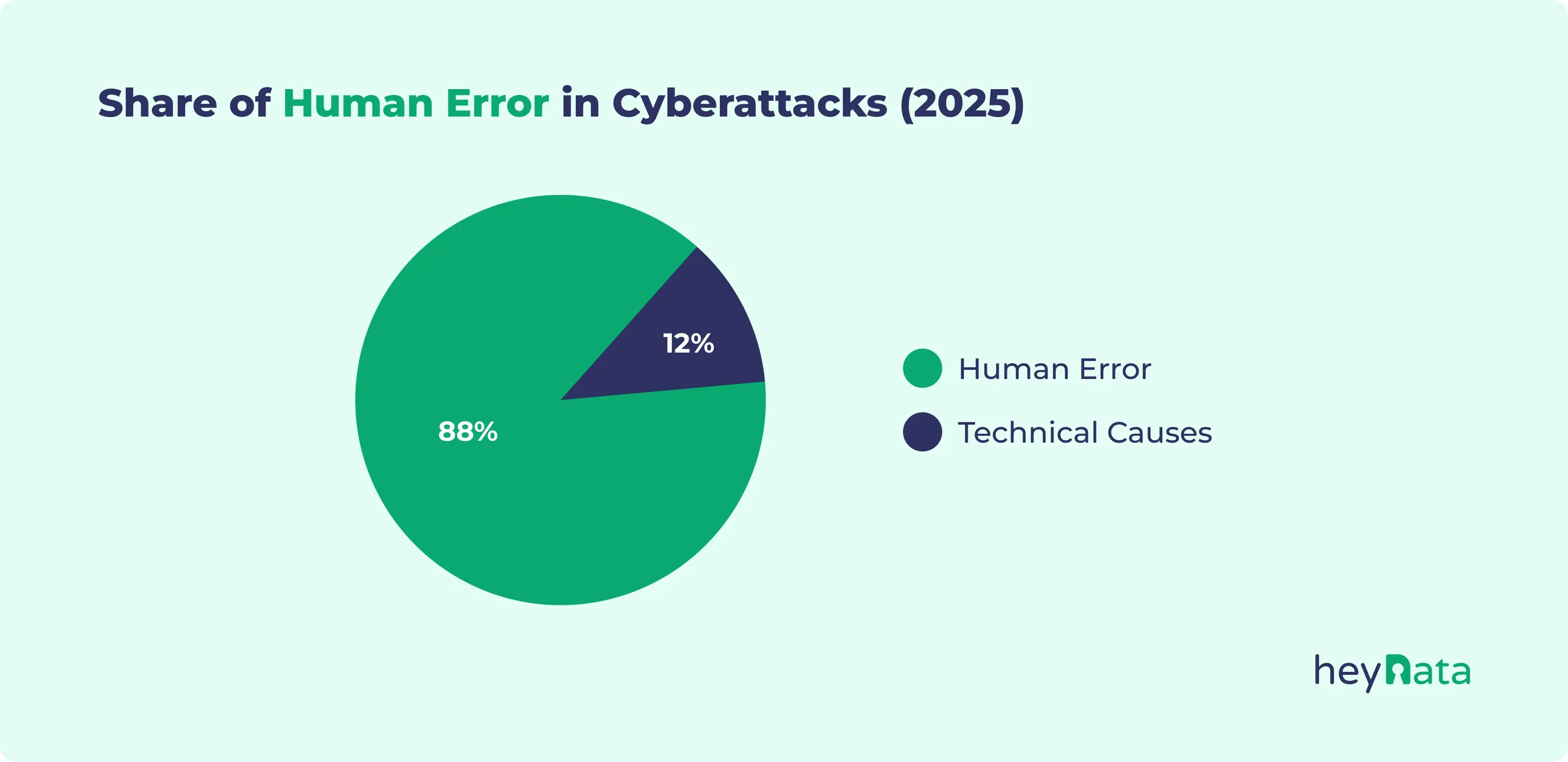
- 88% of cyberattacks have human origins.
- Social engineering and phishing remain the most common entry points.
- Training, MFA, and a strong security culture are essential.
- Compliance tools like heyData support prevention and documentation.
The Human Factor as Cybersecurity’s Weakest Link
The digital threat landscape in 2025 is more complex than ever. Despite technological progress, humans remain the biggest vulnerability in IT security. Studies show that up to 95% of security incidents are linked to human error, from phishing clicks and weak passwords to improper data handling. Attackers deliberately exploit human behavior patterns to gain access.
The consequences of such incidents range from data loss and financial damage to regulatory penalties. Companies can no longer treat human risks as a side issue. Instead, they must integrate them into a holistic security strategy where technical measures and organizational processes work hand in hand.
This article outlines the current state of human-related risks in cybersecurity, highlights data and case studies, and explains how companies can mitigate risks through training, technology, and compliance solutions like heyData.
Table of Contents:
1. The Numbers Don’t Lie: How Severe Is Human Error?
Numerous studies confirm the significance of human mistakes as the main cause of security incidents. According to Stanford University, around 88% of all cyberattacks are directly or indirectly linked to human error. The Verizon Data Breach Investigations Report (2024) adds: In 68% of analyzed cases, a human factor was involved.
Common issues include clicking on phishing links, using weak or reused passwords, or mishandling sensitive data. The financial impact is huge: IBM reported the average cost of a data breach in 2024 was $4.88 million.
These numbers make one thing clear: Cyber defense only works when employees are seen as part of the security strategy and actively engaged.
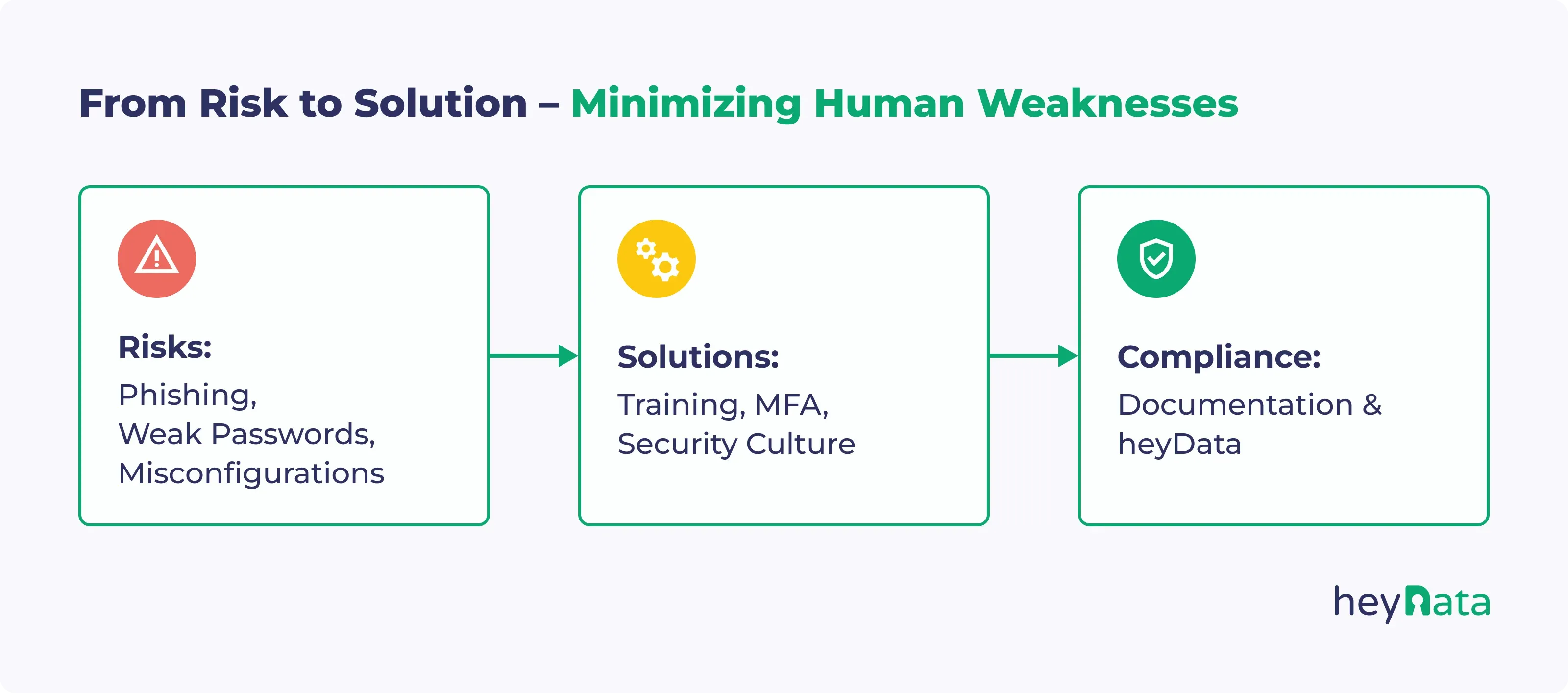
2. The Most Common Human Mistakes
Phishing & Social Engineering
Phishing remains one of the most widespread and effective attack methods. Fraudulent emails or messages mimic trusted senders, tricking employees into revealing sensitive data or clicking malicious links.
Weak or Reused Passwords
Passwords remain a major entry point, especially when they are simple, reused, or publicly exposed. Despite widespread awareness campaigns, weak password practices persist across industries.
Misconfiguration & Data Errors
Unencrypted data, incorrect access rights, or misconfigured cloud services frequently lead to breaches. Often, these issues stem not from bad intent but from a lack of awareness.
Device Loss
Lost or stolen laptops and smartphones pose significant risks, especially when unencrypted or lacking remote-wipe capabilities.
3. Case Studies 2024/2025: When People Fail
- Qantas (Australia, 2025): The airline fell victim to a social engineering attack by the hacker group Scattered Spider. Posing as employees at the helpdesk, the attackers bypassed even two-factor authentication to gain access.
- UK retail sector: Well-known brands like M&S, Harrods, and Co-op were targeted by similar schemes.
- SK Telecom (South Korea): A high-profile case that compromised customer data.
- Episource (USA): A healthcare provider breach affected over 5.4 million people.
These examples show that no company is too large or too “secure” to fall victim to human-related vulnerabilities.
4. Why Training Alone Is Not Enough
Many companies rely on annual training or mandatory onboarding modules. But these measures often fall short. Proofpoint reports that while more than half of companies invest in awareness programs, they are often irregular, not role-specific, and lack real-life relevance.
A common mistake: treating training as a one-off compliance task instead of a continuous process. The result is limited effectiveness. Companies need new formats micro-learning, monthly security nudges, roleplay, and phishing simulations to make security awareness stick.
5. The Solution: A Holistic Approach
Cultural Shift
Cybersecurity must become part of the organizational culture. Leadership plays a critical role; they must make it visible, lead by example, and keep it top of mind.
Regular & Personalized Training
Different teams face different risks. IT staff require different content than HR or Sales. The most effective approaches include targeted micro-training, phishing simulations, and gamified learning.
Technical Enhancements
Multi-factor authentication (MFA), password managers, and endpoint encryption reduce the consequences of human mistakes. Regular access reviews and certifications (e.g., ISO 27001) help identify and fix weaknesses systematically.
AI-Powered Detection
Modern AI tools can detect suspicious behavior in real time, such as unusual login times or irregular email communication. According to Proofpoint, 87% of CISOs plan to increase investment in such tools.
6. Compliance: More Than a “Nice to Have”
Human mistakes in data processing don’t just create technical risks; they carry legal consequences. Regulations like the GDPR and new frameworks (e.g., NIS2, DORA) require clear processes, evidence, and accountability:
- Document training activities
- Report breaches within 72 hours
- Secure third-party vendors via DPAs (Data Processing Agreements)
- Maintain up-to-date records of processing activities
Failure to comply exposes organizations to financial and reputational risk
7. heyData: Compliance Meets Usability
heyData supports companies with a pragmatic digital solution that simplifies compliance and reduces human error risks. The platform provides:
- Automated creation & maintenance of privacy documentation (e.g., processing records, policies)
- Structured management of DPAs with vendors
- GDPR-compliant training modules for employees
- Handling of data subject requests (access, deletion, etc.)
- Updates on regulatory changes (e.g., NIS2, DORA)
heyData doesn’t replace technical defenses like firewalls or SIEM systems. Instead, it serves as the central platform to meet organizational compliance obligations, a crucial building block in minimizing human error.
8. Recommendations for Companies
Blaming employees for breaches misses the point. Usually, the root causes are insufficient training, unclear rules, or poor technical safeguards. It’s the company’s responsibility to ensure staff can work securely.
Short-Term Actions
- Launch phishing-awareness campaigns and measure results
- Roll out or refresh employee security training
- Review and update password & access policies
- Use heyData for DPA management and documentation
- Develop and test an incident-response plan
Long-Term Actions
- Make security awareness a leadership priority
- Integrate cybersecurity into company goals and communication
- Regularly review processes with compliance tools like heyData
- Continuously upskill staff
- Align technical and organizational measures
FAQ – Human Risks in Cybersecurity
What are the most common human mistakes in IT security?
Phishing, weak passwords, misconfigured access, and sending data to the wrong recipients.
How can I improve employee training?
Through regular, role-based, interactive training with simulations and real-life examples. Continuous, not one-off, programs are most effective.
How does heyData support cybersecurity?
heyData provides tools for documentation, training, and DPA management — covering organizational and compliance risks, not technical defenses.
What’s the difference between Cybersecurity and Compliance?
Cybersecurity focuses on technical safeguards. Compliance ensures legal and organizational requirements are met. Both are necessary — heyData covers the compliance side.
What is a DPA (Data Processing Agreement)?
A mandatory GDPR contract with vendors who process data on your behalf. heyData simplifies creation, management, and storage of DPAs.
Conclusion: Cybersecurity Starts with People - Supported by Systems
The threat landscape is constantly evolving, but one factor remains constant: humans are often the entry point. Companies must consistently invest in training, culture, and compliance.
Tools like heyData help organizations meet legal requirements, create transparency, and empower employees. True security arises not from technology alone, but from the interplay of people, processes, and digital tools.



