
Whitepaper on the EU AI Act

SMEs and cybersecurity – the trend report for 2026

'%3e%3cpath%20d='M26.6667%2020.022L30%2023.3553V26.6886H21.6667V36.6886L20%2038.3553L18.3333%2036.6886V26.6886H10V23.3553L13.3333%2020.022V8.35531H11.6667V5.02197H28.3333V8.35531H26.6667V20.022Z'%20fill='%230AA971'/%3e%3c/g%3e%3c/svg%3e) The most important information at a glance
The most important information at a glance
- Cyberattacks are becoming more frequent, cheaper, and more targeted: AI lowers the barriers to entry for attackers, while the damage to companies continues to rise.
- SMEs are becoming the focus of attention, as large corporations are better protected and smaller targets are easier to compromise.
- New legal requirements and regulations are coming into force for companies – but guidelines alone do not provide protection without implementation, awareness of the problem, and appropriate support.
Introduction: The new threat landscape in 2026: Cybersecurity for SMEs
2026 will be a decisive year for cybersecurity – especially for small and medium-sized enterprises. The threat situation is growing rapidly: attacks are becoming more frequent, more technically sophisticated, and significantly cheaper to carry out thanks to AI. At the same time, companies are facing new regulatory requirements and a tense geopolitical situation that is further fueling cybercrime.
While large corporations have massively expanded their security structures, SMEs are increasingly becoming the focus of attackers. They often have limited resources, but are just as dependent on digital processes – and therefore particularly vulnerable.
This paper shows what developments are emerging in 2026, why SMEs are coming under greater pressure, and which strategies really work to minimize risks and measurably increase their own resilience. The aim is to give you a clear, practical overview. What lies ahead for companies, where are the greatest dangers – and how can a significant gain in security be achieved with manageable effort?
Table of Contents:
Cybersecurity 2026 – the most important changes for SMEs
2026 will be a year in which cyberattacks on domestic companies reach a new level. Cyberattacks have been increasing for years; according to IBM, the average cost of a data breach is now over 4.4 million US dollars – and rising. The European perspective is equally alarming. ENISA, the EU Agency for Cybersecurity, analysed around 4,900 significant security incidents in detail between July 2024 and June 2025 and found that not only the number, but also the variety of attack types and methods has reached unprecedented levels.
For attackers, cyberattacks are relatively inexpensive compared to the potential payout: It is true that the maximum, median and average sums companies have to pay their cyber extortionists have recently fallen slightly, but the following problems have intensified, especially for SMEs:
- They have become far more interesting to attackers than large corporations (who are blackmailed for ransom amounts that are orders of magnitude higher), because big corporations now protect themselves much more effectively (precisely because they have been victims in the past). SMEs have become significantly more attractive than corporations for attackers today, because large companies have learned from previous attacks and massively strengthened their defences, while in total, similar ransom amounts can be extracted from SMEs.
- AI enables attackers to launch far more attacks on different targets while their own effort decreases and the use of attack methods (phishing tools, DDoS, exploit kits…) becomes more intensive.
- The dynamic created by 1) and 2) leads to more and more copycats trying their hand as cyber desperados (the “ransomware-as-a-service” phenomenon).
At the same time, the geopolitical climate is intensifying
The ongoing conflict between the Western world and Russia, as well as the rivalry with the BRICS states, is driving targeted cyber operations by criminals from these countries – often funded or supported by state actors whose resources are virtually unlimited. For them, collecting ransom is a welcome side effect, but the primary goal is to create instability in our societies, including economic life.
The problem: Today, we tend to be at the upper end of Maslow’s hierarchy of needs. Our priorities revolve mainly around comfort, status, identity, and self-fulfilment. And these types of needs are not satisfied by simple, but by complex products. We long for AirPods, not pea soup. And complex products lead to complex structures. Supply chains, processes, corporate cultures – all of this significantly increases the attack surface for cyberattacks. Combined with the higher margins of such products, a company becomes a dream target for attackers.
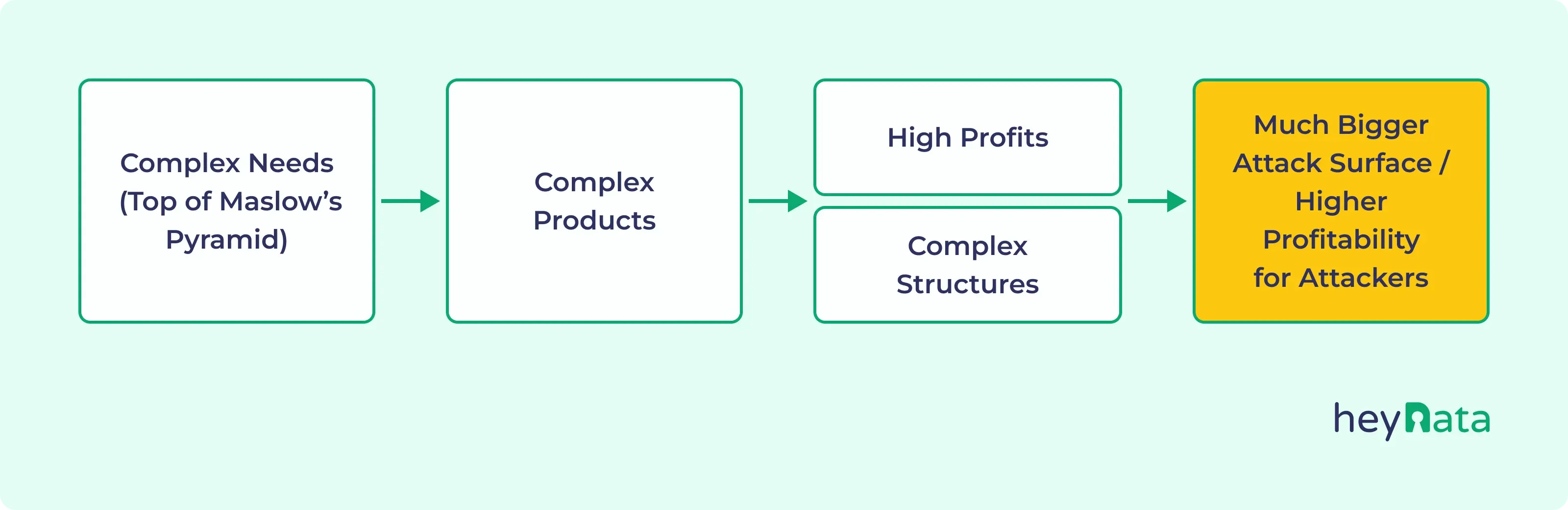
No modern company can afford to say today: “We are not a target.”

Whitepaper on the EU AI Act
What to do? The RTK triad (regulation, technology, culture)
Likewise, no modern company can afford to merely react to regulations and legal requirements and check them off mechanically just to keep the peace.
However, no modern company can afford to merely react to regulations and legal requirements and check them off mechanically just to keep the peace.
Real cybersecurity can only emerge through the interplay of regulation, technology, and culture. Based on our project experience with numerous clients, this triad has proven to be a highly effective combination.
1. Using regulations to your advantage
A large part of the answer to modern cyber threats lies in strategically leveraging existing and upcoming EU regulations. NIS2, the EU AI Act, and ISO 27001 all aim to structurally enhance companies’ cybersecurity capabilities, not only in a B2B but also a B2C context. Anyone who complies with these key standards also signals strength to all business partners.
NIS2 – Unified cybersecurity standards for companies:
- Effective from: Officially since late 2024 and in Germany since 13 September 2025.
- Why it matters: NIS2 makes cybersecurity a management responsibility and introduces minimum standards across the EU. This closes gaps that attackers previously exploited due to inconsistent security levels.
- How it works: Requirements include structured risk management, access controls, reporting processes, and business continuity measures. Regular audits increase security levels across the value chain. Result: greater resilience to cyberattacks due to smaller attack surfaces and reduced downtime risk.
EU AI Act – Trust and control over AI systems:
- Effective from: Implemented gradually since August 2024.
- Why it matters: AI is both a target and a tool for cyberattacks, through manipulated training data, prompt injections, or model misuse. The AI Act ensures transparency and traceability. Anyone using AI must understand and control the risks.
- How it works: Providers must assess risks, verify data quality, conduct monitoring, and fulfil transparency obligations. Additional requirements apply depending on risk class, such as logging, human oversight, or resistance to manipulation.
Result: Reduced attack surfaces in AI-supported processes and greater trust in interactions with business partners.
ISO 27001 – Structure for information security and resilience:
- Effective from: The current version dates to late 2022. It is not mandatory but increasingly expected as a de facto standard.
- Why it matters: ISO 27001 is the global framework for information security. It requires companies to identify risks holistically and continuously improve protective measures.
- How it works: An ISMS (Information Security Management System) defines roles, processes, and technical measures such as access controls, encryption, logging, backup management, and incident response.
Result: Structured prevention against cyberattacks, enabling rapid response in emergencies and demonstrable compliance for stakeholders (particularly relevant for insurance and reinsurance cases).
2. Using technology effectively
In IT, the possibilities for technical tinkering are endless, and you can fail beautifully without ever coming close to achieving your actual goal.
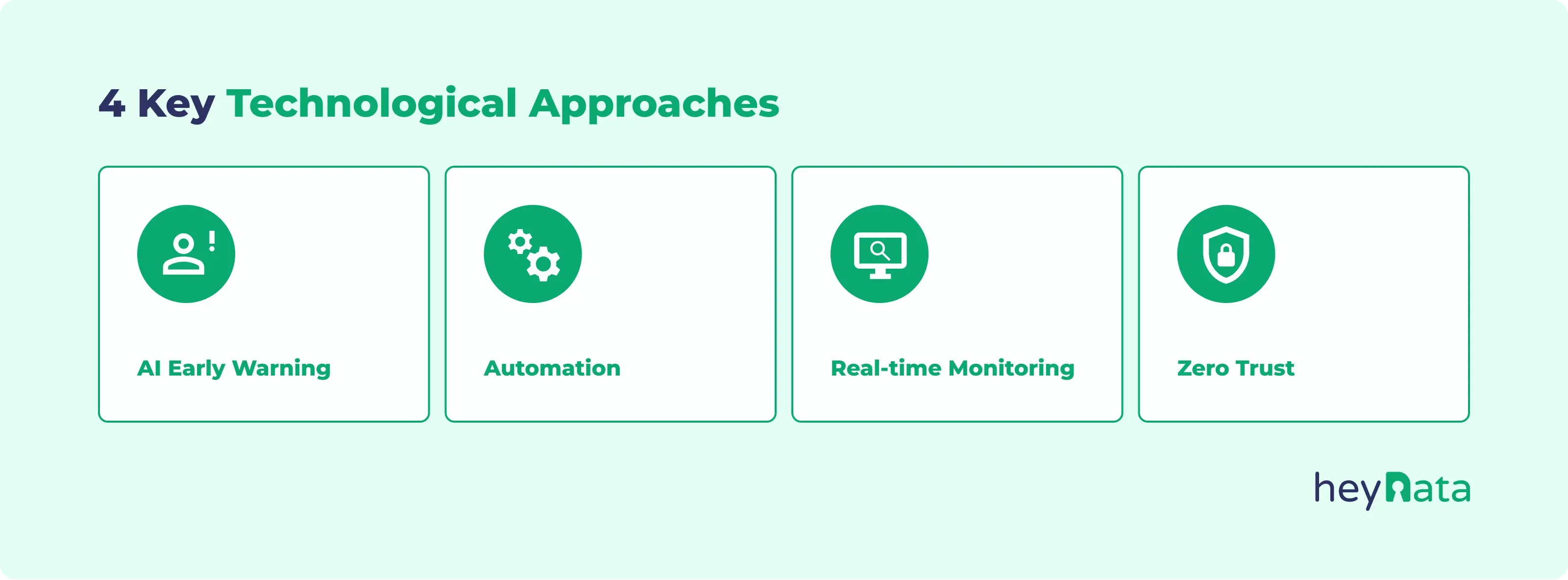
Based on our experience with mid-sized clients - and in the spirit of Pareto - we recommend the following four technological approaches to solve more than 80% of cybersecurity problems:
Using artificial intelligence as an early warning system
AI detects patterns and anomalies in log data, emails, or network traffic. Suspicious activities, such as unusual logins or data leaks, trigger automatic alerts. Benefit for companies: Such AI solutions are becoming increasingly affordable and easier to implement.
Result: Faster and more reliable detection - less damage.
Relieve teams through automation
It’s a familiar issue, security teams are chronically overloaded. Automated tools (which are becoming more affordable) take over patch management, policy reviews, or log analysis and also reduce error rates.
Result: Fewer errors, shorter response times, and the establishment of a higher baseline security level across the company.
Introduce real-time monitoring to prevent escalation
The classic issue many attack attempts go unnoticed for days. Continuous monitoring or SIEM systems collect all logs centrally, detect anomalies, and alert immediately. Result: transparency and responsiveness in real time, dramatically strengthening cyber resilience.
Establish a “Zero Trust” approach
Zero Trust means no one and nothing is trusted automatically. Every request is authenticated, authorized, and encrypted regardless of location.
Result: Even in the event of a successful attack, damage remains minimal.
3. Strengthening corporate culture
Regulation provides the framework, technology delivers the tools, but without a lived security culture, neither becomes effective. True resilience emerges only when security becomes part of the company’s identity. From our projects, we know: with the right cultural levers, this shift can be actively initiated. Here are a few examples:
Get the human risk factor under control
Over 80% of all security incidents begin with human error. Regular awareness trainings, phishing simulations, and clear do’s and don’ts create healthy routines.
Result: Employees transform from vulnerabilities into protective assets.
Define governance & responsibilities
Many security problems arise from unclear accountability. A clear governance model with roles and metrics creates ownership.
Result: Security becomes measurable and firmly embedded in daily operations.
Security as a mindset, not a project
One-off trainings aren’t enough. Recurring rituals like lunch-and-learn sessions, quarterly retros, or tabletop exercises permanently anchor security awareness.
Result: Security becomes a shared responsibility from leadership to support teams.
Conclusion: Cybersecurity is no longer a niche topic but a strategic success factor. All companies must demonstrate results many struggle to do so sufficiently or at all.
The RTK triad is a practical way to gain a real competitive advantage and you meet the requirements of upcoming regulations almost “in passing.”
The Road Ahead: From one-time certification to a continuous process
Certified once and “checked off”? This mindset no longer works in 2026 (not that it worked much better in the past…). The goal is no longer to pass audits, but to become, and remain resilient in a world where cyberattacks grow more complex, targeted, and automated every year. NIS2, the EU AI Act, and ISO 27001 are not ends in themselves or bureaucratic burdens; they are tools to establish minimum standards in the business world in the face of cyber threats.
Today, compliance means keeping pace with attackers and ideally staying ahead of them.
We at heyData can support you in this
Whether implementing policies, conducting risk assessments, or delivering training our mission is to guide companies safely through the digital age.
CHECKLIST: 5 steps you can take to significantly increase your cyber resilience within 72 hours
1. Clarify scope & risks
Identify the most important systems, applications, and data flows — such as email, accounting, cloud services, online shops, or supplier interfaces. Check where sensitive customer or employee data resides and which of it is particularly critical for your business.
Result: You uncover gaps and gain a much clearer understanding of what needs to be protected.
2. Start with an inventory
Create a simple overview of all tools, service providers, and systems that access these critical data assets. Document where potential vulnerabilities or missing security measures exist.
Result: You gain far more transparency regarding potential attack surfaces.
3. Define responsibilities
Decide which central person (e.g., IT manager or data protection coordinator) is best suited to consolidate, document, and prioritize your security topics. Consider what authority they need. Define escalation paths and backups for emergencies.
Result: You manage cybersecurity as an active, structured topic.
4. Raise team awareness
Regularly(!) inform all employees about the most common risks: phishing, weak passwords, and unsecured devices. This can be done through short online awareness sessions or on-site trainings.
Result: You actively reduce the human risk factor.
5. Implement quick wins
Where possible, activate multi-factor authentication (MFA), actually apply any outstanding software updates, and check whether your backups are functioning properly. These three steps alone drastically reduce your attack surface within hours.
Result: You achieve an immediate, measurable, and demonstrable security improvement.

Closing remarks
Cyberattacks continue to increase and evolve faster than traditional compliance models can keep up. At heyData, we help you turn what is perceived as a burdensome obligation into a competitive advantage.



