
Get expert privacy tips and compliance guidance

Top Data Breaches and Privacy Scandals of 2025 (So Far)
'%3e%3cpath%20d='M26.6667%2020.022L30%2023.3553V26.6886H21.6667V36.6886L20%2038.3553L18.3333%2036.6886V26.6886H10V23.3553L13.3333%2020.022V8.35531H11.6667V5.02197H28.3333V8.35531H26.6667V20.022Z'%20fill='%230AA971'/%3e%3c/g%3e%3c/svg%3e) Key Takeaways at a Glance
Key Takeaways at a Glance
- In 2025, major data breaches hit companies like 23andMe (genetic data), Samsung (customer records), TikTok (data transfers), Coinbase, Facebook, Amazon, and Meta.
- Highly sensitive data—including genetic, ID, account, and behavioral information—was especially at risk.
- Main causes included third-party mistakes (e.g., Dior, Hertz), outdated vulnerabilities, and lack of proper consent (e.g., Amazon, TikTok).
- Regulatory penalties and public scrutiny increased significantly, with record fines for TikTok, Meta, and Apple.
- Businesses must prioritize data protection: transparency, rapid response, and data minimization are essential.
The first half of 2025 has seen a sharp rise in major data breaches. From genetic data leaks to massive social media account dumps, companies across a wide range of industries have struggled to protect the personal information they collect and store.
The incidents reported so far show a clear trend toward larger breaches involving more sensitive categories of data. Instead of just usernames and passwords, we’re seeing leaks that expose genetic profiles, voice recordings, and biometric identifiers. This data is not only deeply personal but also difficult or impossible to change once compromised. Cybercriminals are also targeting systems that have known but unresolved vulnerabilities. These aren’t sophisticated zero-day attacks. Instead, many exploit simple vulnerabilities and oversights, such as weak passwords, outdated software, or misconfigured cloud services.
At the same time, regulators are taking a tougher stance. The penalties for violating the GDPR have become more severe, and companies are finding themselves under pressure to demonstrate real, ongoing compliance.
Lastly, public awareness is also increasing. Users are more informed about their data rights, and breaches now receive widespread media attention. As a result, even a small data leak can cause long-term damage to customer trust.
In this article, we'll explore the major data breaches of 2025 to date, and draw practical lessons to help companies avoid similar outcomes.
Table of Contents:
The Most Serious Data Breaches in 2025 So Far
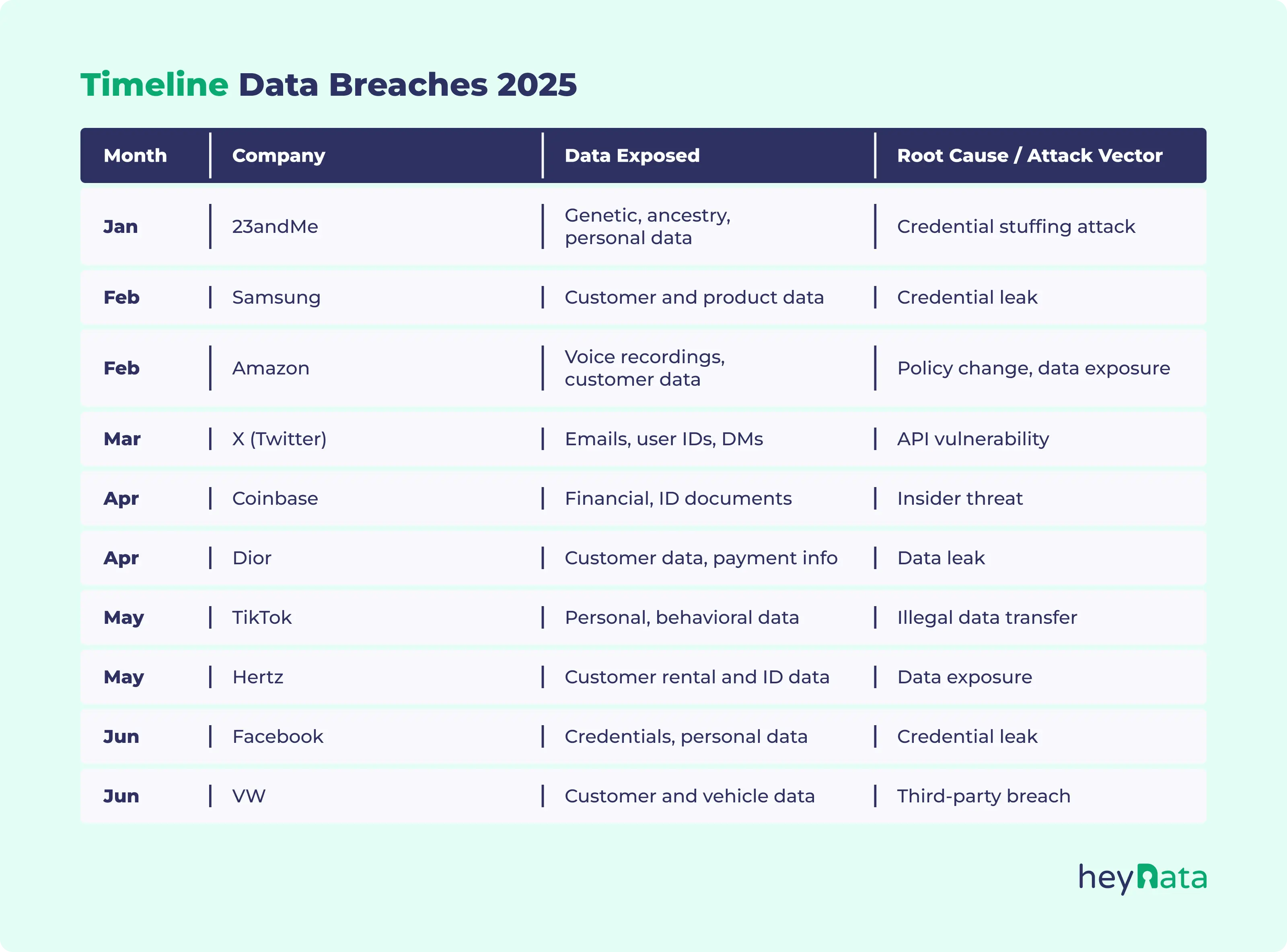
1. 23andMe: Genetic Data Sold and Leaked
In 2023, DNA testing company 23andMe faced criticism after hackers leaked and sold detailed genetic information tied to user identities. The breach came to light after samples of the stolen data were posted for sale on dark web forums. The data included names, contact details, genetic makeup, and ancestry profiles. Reportedly, over 7 million user records were affected.
More recently, in March 2025, the company faced renewed criticism after declaring bankruptcy. According to the company, the bankruptcy will not affect how it stores and manages personal data. However, the company's privacy policy allows personal data to be disclosed to third parties regardless of whether consent is given.
Genetic data is uniquely sensitive, not only because it contains health-related information, but also because it implicates relatives who have not consented. In the EU, such data is classified as special category data under the GDPR and cannot legally be used by insurers or employers. However, direct-to-consumer services like 23andMe fall into a regulatory grey zone. Unlike medical providers, they’re not held to the same strict confidentiality rules. Worse, one person’s consent can compromise the privacy of their entire biological family.
The bankruptcy of 23andMe raises further concerns about how this high-risk data will be handled, stored, or potentially sold in the absence of strong legal regulations.
2. Samsung: 270,000 Customer Records Leaked
In March 2025, Samsung experienced a breach involving the theft and leak of 270,000 customer records.
The stolen data included names, email addresses, phone numbers, order numbers and product details (such as TV models) as well as customer complaints and Samsung's responses. The leaked data was stolen from Samsung Germany.
The attackers reportedly gained access through a set of credentials that had been compromised as far back as 2021, when a Samsung partner employee was infected with malware. The malware harvested login details from the employee’s device. Although cybersecurity firm Hudson Rock flagged the exposed credentials to Samsung years ago, Samsung reportedly failed to rotate or secure them. As a result, the same credentials remained active and exploitable, ultimately enabling the attacker to breach Samsung’s systems and leak sensitive data in 2025.
This highlights how easily dormant accounts can become entry points for cyberattacks.
In this case, it's important to highlight how a company as large and well-resourced as Samsung still failed to follow basic security hygiene. This breach shows that scale does not equal immunity. Legacy systems and forgotten user accounts can introduce major risks.
3. Amazon Echo: Voice Data Privacy Concerns
On March 28, 2025, Amazon announced it was discontinuing the “Do Not Send Voice Recordings” setting on Echo devices that support on-device storage. Going forward, all user interactions with Alexa devices will be recorded and sent to Amazon’s servers by default, with no option to opt out. The change coincides with the rollout of Alexa+, Amazon’s new generative AI assistant designed to offer more advanced, context-aware conversations.
According to Amazon, sending recordings to the cloud is necessary to support the enhanced capabilities of Alexa+, which include remembering past conversations, understanding complex queries, and offering more personalized assistance. However, this also means that users will no longer have control over whether their voice commands are stored and analyzed, a move that has sparked privacy concerns from consumer rights groups and digital privacy advocates alike.
Critics argue that removing the opt-out undermines user autonomy and opens the door to deeper surveillance, especially as Alexa+ is expected to be more deeply integrated into users’ daily lives. The decision raises fresh questions about how long Amazon will retain this data, how it will be used to train AI models, and whether it could be shared with third parties or used in targeted advertising.
From a GDPR perspective, this policy sparked debate about whether such a decision violated the GDPR’s requirements for freely given, specific, informed, and unambiguous consent. Since users could not refuse the data collection while continuing to use the product, the legal grounds for processing became questionable.
4. X (Twitter): 200 Million User Records Released
In March 2025, a hacker released a massive dataset containing 200 million X (formerly Twitter) user records, including email addresses, handles, and user IDs.
The origins of the leak trace back to a vulnerability first reported to Twitter’s bug bounty program in January 2022, which allowed attackers to match phone numbers or email addresses to Twitter accounts through an unprotected API. Although Twitter acknowledged the issue and took action, it later confirmed that attackers had already exploited the vulnerability to scrape massive amounts of user data.
Now, in 2025, that same data has resurfaced. A data enthusiast claims to have accessed the original scraped dataset and merged it with a more recent breach, publishing it as a unified dump of 200 million user profiles.
Social media platforms are attractive targets because of the volume of data and the potential for impersonation, phishing, or social engineering. In this case, an unpatched vulnerability led to the repeated exposure of sensitive user metadata, three years after the issue was first identified.
The lesson from this story is that APIs must be secured just like any other attack surface, such as websites and apps. Companies should implement strict rate limiting, validation checks, user authentication, and regular testing to prevent data scraping and abuse. Vulnerabilities identified through bug bounty programs must be acted on immediately, as delays give attackers the time they need.
5. Coinbase: Customer Data Breach
In May 2025, Coinbase disclosed a significant data breach involving the theft of sensitive customer information. The breach was carried out by cybercriminals who bribed overseas contractors or employees in support roles to access internal Coinbase systems. Approximately 510,000 customers were affected.
The stolen data included customer names, postal and email addresses, phone numbers, the last four digits of Social Security numbers, masked bank account numbers, banking identifiers, government-issued identity documents (such as driver's licenses and passports), account balances, and transaction histories. Additionally, some internal corporate documentation was compromised.
The attackers demanded a $20 million ransom to prevent the public release of the stolen data. Coinbase refused to pay the ransom and instead offered a $20 million reward for information leading to the capture of the perpetrators. The company estimates that the incident could cost between $180 million and $400 million in remediation and customer reimbursements.
This breach highlights the vulnerabilities associated with outsourcing support roles, especially when contractors have access to sensitive data. It underscores the importance of access controls and monitoring of third-party vendors to prevent insider threats.
6. Dior: Unauthorised Data Leak in China
In May 2025, Dior issued a public apology following an unauthorized data leak involving its Chinese customer base.
The breach exposed personal information, including names, contact details, and purchase histories, of customers who had interacted with Dior's services in China. The company acknowledged that the leak resulted from a third-party vendor's failure to adhere to data protection protocols, leading to unauthorized access and dissemination of sensitive customer data.
Dior stated that it had promptly initiated an internal investigation upon discovering the breach and took immediate steps to contain the incident. The company emphasized its commitment to protecting customer information and announced plans to enhance its data security measures to prevent future occurrences. Additionally, Dior reported the incident to relevant regulatory authorities and pledged full cooperation with ongoing investigations.
This is another example highlighting the vulnerabilities that can arise from third-party partnerships, especially when handling sensitive customer data.
7. TikTok: €530 Million Fine for Sending Data to China
In May 2025, TikTok was fined €530 million by Ireland’s Data Protection Commission (DPC) for illegally transferring the personal data of approximately 1.1 million users, many of them minors, to servers in China. The data included names, contact information, behavioral metadata, and device identifiers. The DPC determined that TikTok failed to ensure adequate protection for European users' data when transferring it to China, where surveillance laws grant authorities broad access to corporate data.
Additionally, between 2020 and 2022, TikTok did not inform users that their data was being transferred to China, breaching GDPR transparency requirements. Although TikTok updated its privacy policy in 2022 to address this issue, the DPC noted that the company had provided conflicting information about data storage locations.
This ruling marks the EU's first significant action against data transfers to China, emphasizing the need for companies to ensure that international data transfers comply with EU privacy standards. It highlights the growing scrutiny of how global tech companies handle European user data, especially concerning jurisdictions with differing surveillance laws.
The takeaway here is that organizations must conduct thorough assessments of foreign legal frameworks when transferring data internationally. Transparency with users about data handling practices is crucial, and companies should implement strong measures to align with regional data protection regulations.
8. Hertz: Breach via Cleo File Sharing Tool
In early 2025, Hertz, a car rental company, disclosed a significant data breach resulting from a vulnerability in Cleo, a file-sharing service used by Hertz. The cyberattack, occurring between October and December 2024, compromised sensitive customer information, including names, contact details, dates of birth, driver's license numbers, credit card details, and, in some cases, Social Security numbers, passport information, and workers' compensation data. The breach exposed over 100,000 customer records across various regions, including the U.S., Canada, the EU, the UK, and Australia.
This is another incident that underscores the risks associated with third-party vendors and the importance of strong cybersecurity measures, even when outsourcing services. Companies must conduct thorough due diligence when selecting third-party vendors, ensuring they implement and maintain strong cybersecurity practices. Regular audits, vulnerability assessments, and clear contractual obligations regarding data protection are essential to mitigate risks associated with supply chain attacks.
9. Facebook: 1.2 Billion Records Leaked
In May 2025, a hacker claimed to have scraped a massive dataset containing 1.2 billion Facebook user records by exploiting one of the platform's APIs. The dataset, which was posted on a popular data leak forum, allegedly includes user IDs, names, email addresses, usernames, phone numbers, locations, birthdays, and genders.
Cybersecurity researchers from Cybernews analyzed a sample of 100,000 records from the dataset and found the data to be legitimate. However, they cautioned that the claim of 1.2 billion records could not be independently verified.
Meta, the parent company of Facebook, did not dispute the breach outright but implied that the individuals behind it were merely scammers repackaging an old dataset to make it appear like a fresh leak.
If confirmed, this would be one of the largest data scrapes in Facebook's history, raising serious concerns about the platform's ability to protect user data from unauthorized collection through its APIs.
10. 184 Million Record Leak: Microsoft, Apple, Google, and PayPal Affected
In May 2025, a cybersecurity researcher uncovered a massive data breach involving a 47GB unprotected Elasticsearch database containing over 184 million records. The exposed data included login credentials for major platforms such as Microsoft, Apple, Google, Facebook, PayPal, and Netflix, as well as government and corporate email addresses from at least 29 countries.
The database, which lacked password protection and encryption, also contained credentials for bank accounts, health platforms, and government websites, posing significant security threats to affected individuals. The researcher reported the database to Website Planet, and after alerting the hosting provider, World Host Group, access to the database was disabled to prevent further data exposure.
While the exact duration of the database's exposure remains unknown, the researcher noted that the records appeared consistent with data exfiltrated by infostealer malware. However, there is no confirmed evidence of internal compromise or active misuse of user data at this time.
This breach underscores the growing scale and severity of credential harvesting operations, which can lead to identity fraud, unauthorized access, and widespread corporate breaches.
11. Meta: €200 Million Fine for 'Consent or Pay' Model
In April 2025, the European Union fined Meta €200 million for its implementation of a "consent or pay" model on platforms like Facebook and Instagram. This model required users to either consent to extensive data collection for personalized advertising or pay a subscription fee to avoid such tracking. The European Commission determined that this approach did not provide users with a genuine choice regarding their data, thereby violating the General Data Protection Regulation (GDPR).
This case highlights the importance of obtaining clear and freely given consent for data processing activities. Mechanisms that pressure users into consenting by imposing a financial penalty undermine the principle of voluntary consent enshrined in the GDPR. Implementing models that effectively force users to choose between their privacy and access to services can lead to significant penalties.
To learn more about this case, read our in-depth blog about it.
12. Apple: €500 Million Fine for App Store Restrictions
In April 2025, Apple was fined €500 million by the European Union for breaching the Digital Markets Act (DMA). The fine was imposed due to Apple's restrictions on its App Store, which limited developers from informing users about alternative purchasing options outside of the App Store ecosystem. This practice was found to stifle competition and maintain Apple's dominant position in the market.
The enforcement of the DMA represents a significant step by the EU to promote fair competition in digital markets. Apple's restrictions not only affected developers' ability to compete but also limited consumer choice and potentially led to higher prices.
The lesson here is that companies operating in digital markets must comply with regulations that promote transparency and competition. Restrictive practices that hinder users from accessing alternative services or pricing information can result in substantial fines and damage to their reputation.

Get expert privacy tips and compliance guidance
5 Key Lessons for Businesses from the 2025 Data Breaches
The first half of 2025 has shown clear and consistent patterns in how data breaches occur and how they could have been prevented. Across industries, scales, and geographies, the same critical lessons are repeating:
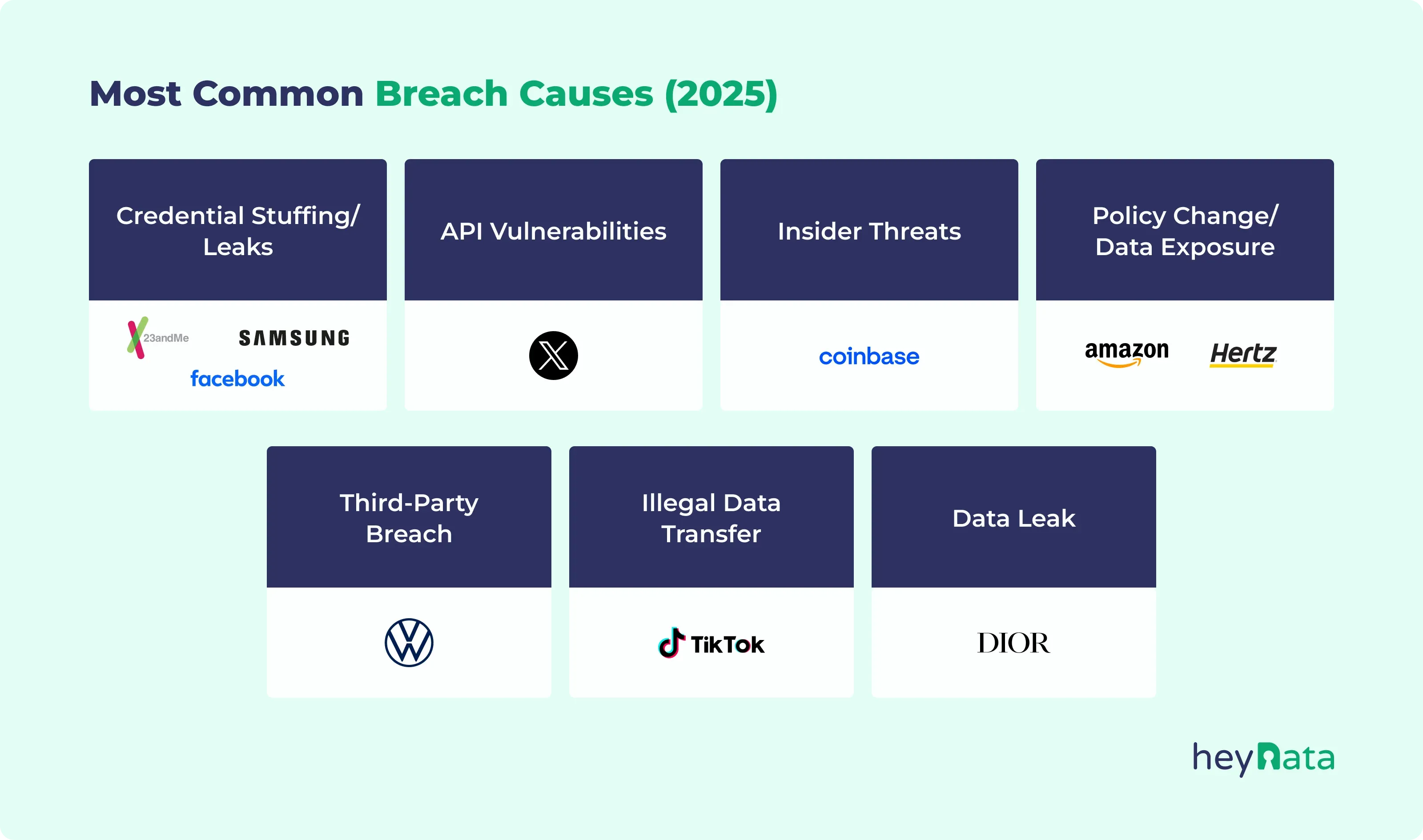
- Third-party risk is underestimated: Breaches at Dior, Coinbase, Hertz, and Samsung all stemmed from outsourced partners or external service providers. When vendors are granted access to sensitive systems or customer data, they become part of your risk surface. Yet many companies still fail to audit them properly or enforce strong security standards.
What to do: Conduct rigorous due diligence on vendors, include clear data protection clauses in contracts, and perform regular security audits. Ensure that data access is based on the principle of least privilege. To find GDPR-compliant vendors, use heyData's Vendor Risk Management solution.
- Known vulnerabilities go unpatched for years: Whether it’s leaked credentials from 2021 (Samsung) or an API vulnerability reported in 2022 (X/Twitter), many of the breaches stemmed from old, unresolved issues. Organizations are either unaware of their vulnerabilities or, worse, aware but complacent.
What to do: Implement a strict vulnerability management program. Track all reported weaknesses, patch quickly, and rotate credentials regularly. Dormant access points are often the weakest link.
- Data minimization is still not a priority: The more sensitive the data, the greater the risk. From genetic profiles to full identity documents and account balances, many of these breaches involved excessive amounts of deeply personal information.
What to do: Limit the collection of sensitive data to only what’s necessary for the service. Regularly review what’s stored, why, and for how long. Delete what you no longer need, and pseudonymize wherever possible.
- Consent is often manipulated or removed entirely: Amazon's elimination of opt-out settings for Alexa and TikTok’s undisclosed transfers to China show how companies bypass user autonomy. This not only invites legal scrutiny but also deeply damages trust.
What to do: Respect the spirit of data protection laws, not just the letter. Ensure consent is freely given, specific, informed, and unambiguous. Be transparent about changes, and offer meaningful choices.
- The cost of failure is rising: From TikTok’s €530 million fine to Coinbase’s projected $400 million remediation costs, regulators are raising the stakes, and so are the customers. A breach now means more than financial loss - it’s reputational damage, legal exposure, and a loss of public trust.
What to do: View data protection as a business-critical function, not a checkbox. Invest in security infrastructure, training, and compliance as ongoing priorities — not one-off tasks.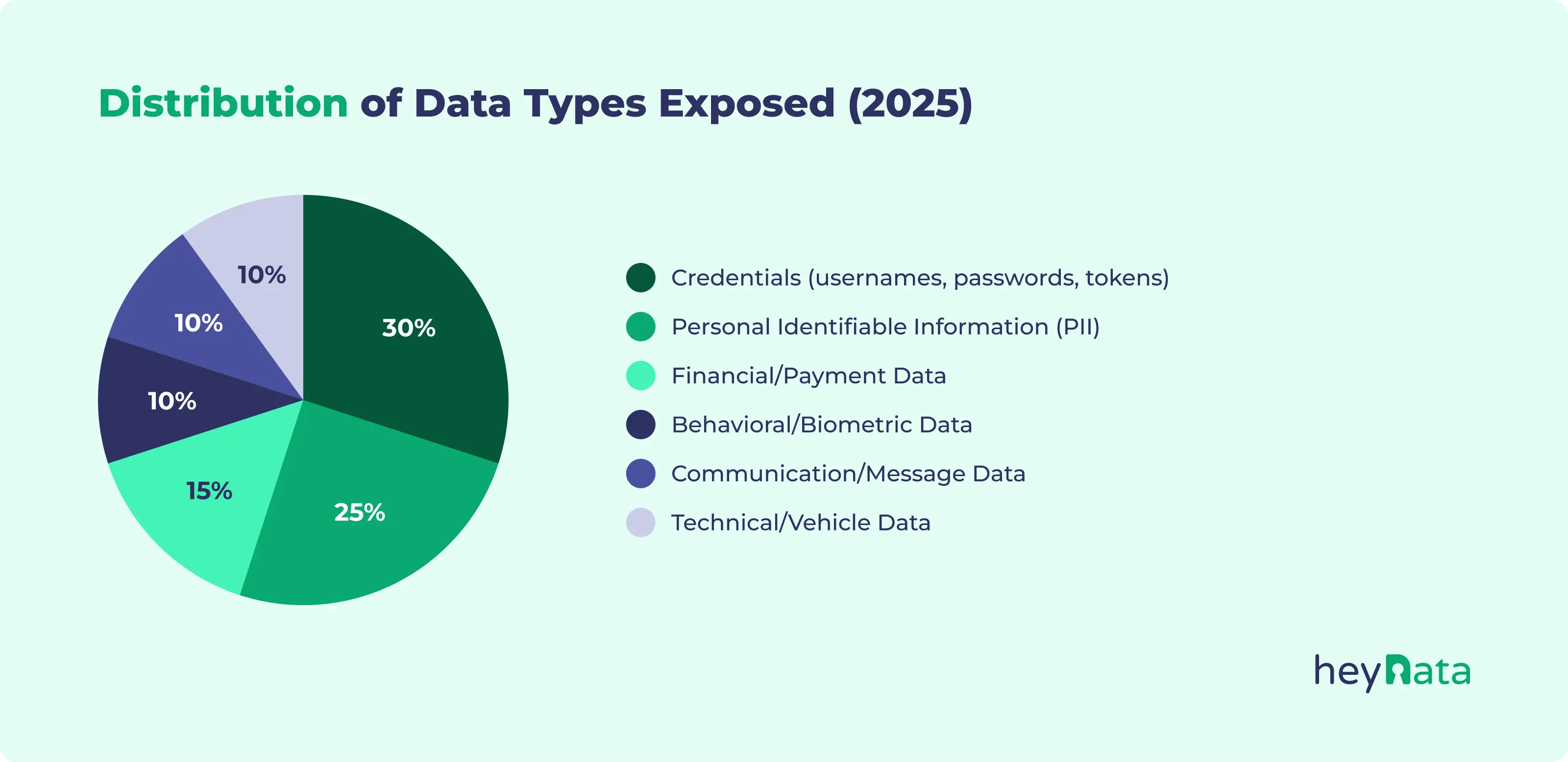
Conclusion
The breaches of 2025 aren’t revealing new threats; they’re reinforcing old truths. Basic security hygiene, strong vendor controls, transparent data handling, and prompt remediation are no longer “best practices” but rather survival requirements. Businesses that internalize these lessons and act decisively will be the ones best positioned to avoid becoming the next headline.
If your company handles personal data, now is the time to review your internal practices, policies, and systems.
Use the examples in this article to identify your weaknesses and take meaningful steps to strengthen them. And if you need help navigating the process, heyData's All-in-One Compliance Solution combines intuitive software and legal expertise to help you master data protection, cybersecurity, and AI compliance.
Frequently asked questions (FAQs)
What is a data breach?
A data breach is the unauthorized access, copying, disclosure, or theft of personal data, often via hacking or employee/vendor mistakes.
What were the biggest data breaches in 2025?
Top incidents involved companies like 23andMe (genetic data), Samsung, Coinbase, Facebook, TikTok, Meta, Apple, and Amazon.
What penalties do companies face for serious breaches?
Under the GDPR, fines can reach hundreds of millions of euros (e.g., €530M for TikTok, €500M for Apple).
How can companies protect themselves from data leaks?
Key actions include partnering with secure vendors, performing regular security updates, minimizing the collection of data, enforcing strict access controls, and educating employees.
What are the risks for affected individuals?
Risks include identity theft, fraud, personal harm, and loss of control over one’s data, often resulting in lasting distrust in the company.
What should you do after a data breach?
Report immediately to authorities, inform affected users quickly and, remediate the vulnerability, and implement stronger protections to prevent recurrence.
Important: The content of this article is for informational purposes only and does not constitute legal advice. The information provided here is no substitute for personalized legal advice from a data protection officer or an attorney. We do not guarantee that the information provided is up to date, complete, or accurate. Any actions taken on the basis of the information contained in this article are at your own risk. We recommend that you always consult a data protection officer or an attorney with any legal questions or problems.


