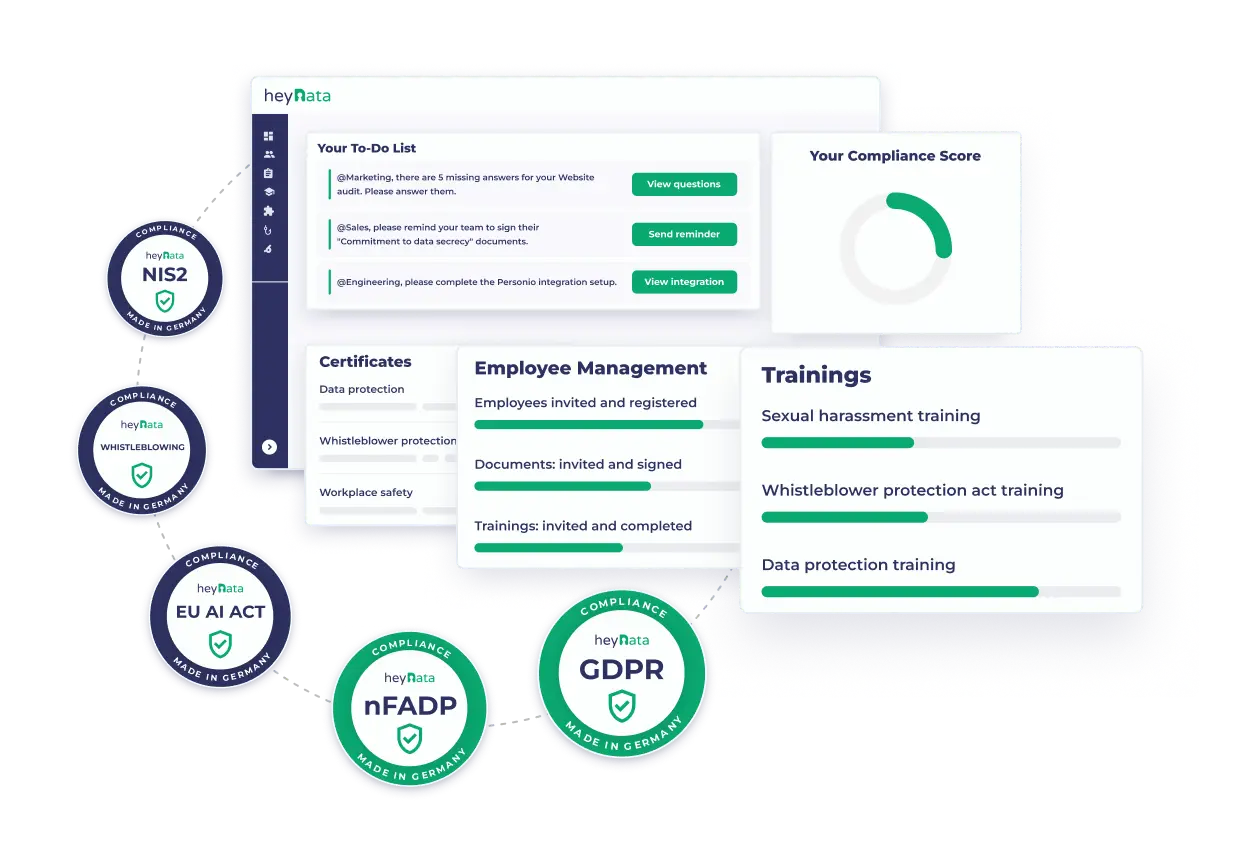
More than 2,000 companies rely on the comprehensive compliance solution from heyData






Your Compliance Requirements – All on One Platform
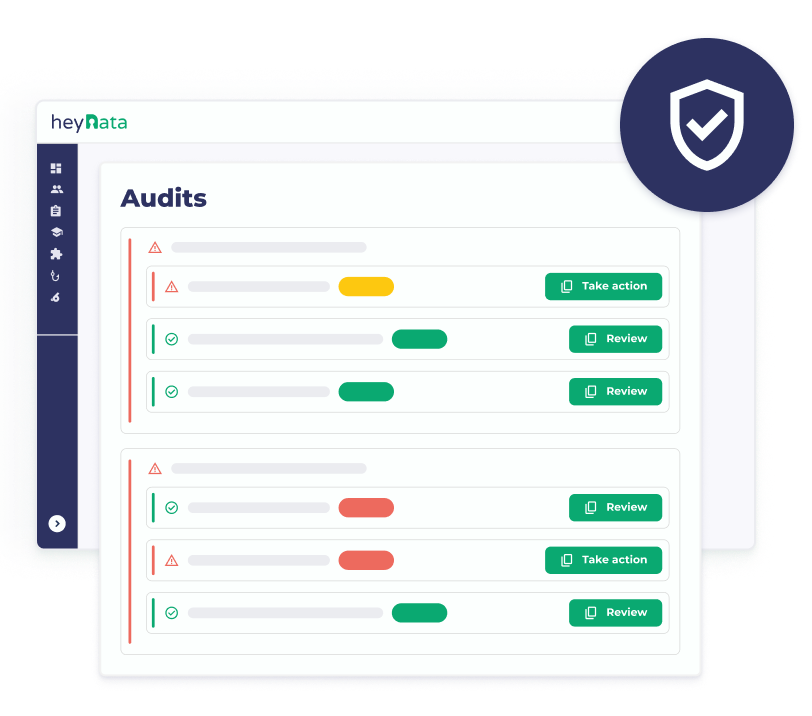
Effective Risk Management for Enhanced Security
Regular audit checks, a central dashboard, and automated processes make risk management with heyData easy and efficient. You stay in control, strengthen security, and relieve your team.

Rely on Expert Knowledge
heyData helps you achieve your compliance goals faster and easier. Our experienced experts support you with GDPR, NIS2, ISO 27001, and more – practically, reliably, and always up to date.

Strong Compliance Starts With Your Team
heyData effectively prepares your employees for compliance. Our training courses are practical, cover the most important regulations and end with a certificate.